Embark on a journey to master the art of load balancer configuration, a crucial skill for any modern web developer. This guide delves into the intricacies of distributing network traffic efficiently, ensuring optimal performance, scalability, and high availability for your applications. We’ll explore the fundamental concepts, various types of load balancers, and the algorithms that govern their operation, setting the stage for a deep dive into practical implementation.
From understanding the core principles of load balancing to configuring hardware, software, and cloud-based solutions, this resource provides a comprehensive roadmap. We’ll navigate the complexities of health checks, advanced techniques like session persistence, and essential security considerations. Get ready to transform your applications into robust, resilient systems capable of handling even the most demanding traffic loads.
Introduction to Load Balancing
In the dynamic landscape of modern web applications, ensuring optimal performance, reliability, and scalability is paramount. Load balancing emerges as a critical technique to achieve these goals. It intelligently distributes network traffic across multiple servers, preventing any single server from becoming overwhelmed and ensuring a smooth user experience.Load balancing, at its core, is the process of distributing network traffic across a group of servers, or resources.
A load balancer is a device or software that acts as a traffic manager, sitting in front of a group of servers and directing client requests to the appropriate server. Its primary function is to distribute incoming client requests efficiently across multiple server instances, thereby optimizing resource utilization, minimizing response time, and preventing any single server from being overloaded.
Benefits of Employing Load Balancing
Load balancing offers significant advantages for web applications and services, contributing to enhanced performance, scalability, and high availability.
- Improved Performance: By distributing the workload, load balancing prevents individual servers from becoming bottlenecks. This results in faster response times and improved overall application performance. For example, an e-commerce website experiencing a surge in traffic during a flash sale can use load balancing to ensure that all users experience minimal delays when browsing products, adding items to their carts, or completing purchases.
- Scalability: Load balancing enables applications to scale horizontally, meaning adding more servers to handle increased traffic. As demand grows, additional servers can be easily integrated into the load balancing configuration, ensuring that the application can handle the increased load without performance degradation. A popular social media platform can dynamically add servers to accommodate a spike in user activity, such as during a major news event, without impacting user experience.
- High Availability: Load balancers continuously monitor the health of the servers in the pool. If a server fails, the load balancer automatically redirects traffic to the remaining healthy servers, ensuring that the application remains available. This redundancy minimizes downtime and ensures that users can continue to access the service even in the event of server failures. Consider an online banking application.
If one of the application servers experiences an outage, the load balancer seamlessly reroutes user requests to the other servers, allowing customers to continue accessing their accounts and performing transactions without interruption.
Types of Load Balancers
Load balancers come in various forms, each designed to address specific needs and environments. Understanding the different types and their characteristics is crucial for selecting the most appropriate solution for a given application or infrastructure. This section will explore the primary categories of load balancers, highlighting their features, advantages, disadvantages, and suitable use cases.
Hardware Load Balancers
Hardware load balancers are physical appliances, typically purpose-built devices, designed for high performance and reliability. They are deployed within the network infrastructure and handle traffic distribution at the hardware level.Hardware load balancers offer several advantages:
- High Performance: They are optimized for processing a large volume of traffic and handling complex load balancing algorithms, delivering exceptional performance.
- Dedicated Resources: They have dedicated hardware resources, ensuring consistent performance and avoiding resource contention with other applications.
- Security Features: They often include advanced security features like DDoS protection, web application firewalls (WAFs), and SSL offloading.
- Scalability: They can scale to handle significant traffic loads, often supporting hundreds of thousands or millions of connections per second.
However, hardware load balancers also have some drawbacks:
- Cost: They are typically the most expensive type of load balancer, involving upfront hardware costs, maintenance fees, and potential vendor lock-in.
- Limited Flexibility: They can be less flexible than software-based solutions, making it more challenging to adapt to rapidly changing requirements.
- Physical Infrastructure: They require physical space, power, and cooling, increasing operational overhead.
- Management Complexity: They may require specialized expertise for configuration and management.
Hardware load balancers are most suitable for:
- High-traffic websites and applications: Where performance and scalability are critical requirements. For example, large e-commerce platforms like Amazon or eBay often use hardware load balancers to handle massive traffic during peak seasons.
- Organizations with complex network infrastructures: Where advanced features like DDoS protection and WAFs are necessary. Financial institutions or government agencies may require the enhanced security capabilities of hardware load balancers.
- Environments where predictable performance is essential: For example, online gaming platforms.
Software Load Balancers
Software load balancers are applications that run on commodity hardware or virtual machines. They provide load balancing functionality using software-defined logic.Software load balancers offer the following benefits:
- Cost-Effectiveness: They are generally less expensive than hardware load balancers, as they utilize existing hardware resources.
- Flexibility: They are more adaptable to changing needs, with easier configuration and updates.
- Portability: They can be deployed on various platforms, including on-premises servers, virtual machines, and cloud environments.
- Automation: They often integrate with automation tools, allowing for easier deployment and management.
However, software load balancers also have limitations:
- Performance: They can be limited by the underlying hardware resources and may not achieve the same level of performance as hardware load balancers.
- Resource Consumption: They consume server resources, potentially impacting the performance of other applications running on the same hardware.
- Management Overhead: They require careful configuration and ongoing maintenance to ensure optimal performance and availability.
- Scalability: Scaling software load balancers can be more complex than scaling hardware load balancers, potentially requiring more manual intervention.
Software load balancers are well-suited for:
- Organizations with budget constraints: Where cost-effectiveness is a priority.
- Environments with virtualized infrastructure: Where flexibility and portability are essential. For example, a company migrating its applications to a cloud environment may opt for software load balancers.
- Applications with moderate traffic loads: Where the performance requirements are not as demanding as in high-traffic scenarios.
- Testing and development environments: Where rapid deployment and configuration are needed.
Cloud-Based Load Balancers
Cloud-based load balancers are managed services offered by cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). They provide load balancing as a service, allowing users to offload the complexities of load balancer management.Cloud-based load balancers offer numerous advantages:
- Scalability: They automatically scale to handle fluctuating traffic demands, eliminating the need for manual intervention.
- High Availability: They are designed for high availability, with built-in redundancy and failover mechanisms.
- Simplified Management: They offer easy-to-use interfaces and automated configuration, reducing the operational overhead.
- Cost-Effectiveness: They often have pay-as-you-go pricing models, making them cost-effective for various use cases.
However, cloud-based load balancers also have potential drawbacks:
- Vendor Lock-in: Users may become dependent on a specific cloud provider, potentially limiting their flexibility.
- Cost Considerations: While offering pay-as-you-go pricing, costs can accumulate, particularly for high-traffic applications.
- Limited Customization: Users may have less control over the underlying infrastructure and configuration options compared to self-managed solutions.
- Dependency on the Cloud Provider: Availability and performance depend on the reliability of the cloud provider’s infrastructure.
Cloud-based load balancers are ideal for:
- Organizations already using cloud services: Where seamless integration and ease of management are important.
- Applications with fluctuating traffic demands: Where automatic scaling is essential. For instance, a news website might use a cloud load balancer to handle traffic spikes during breaking news events.
- Businesses seeking to reduce operational overhead: Where they want to offload the complexities of load balancer management.
- Startups and small businesses: Due to their cost-effectiveness and ease of use.
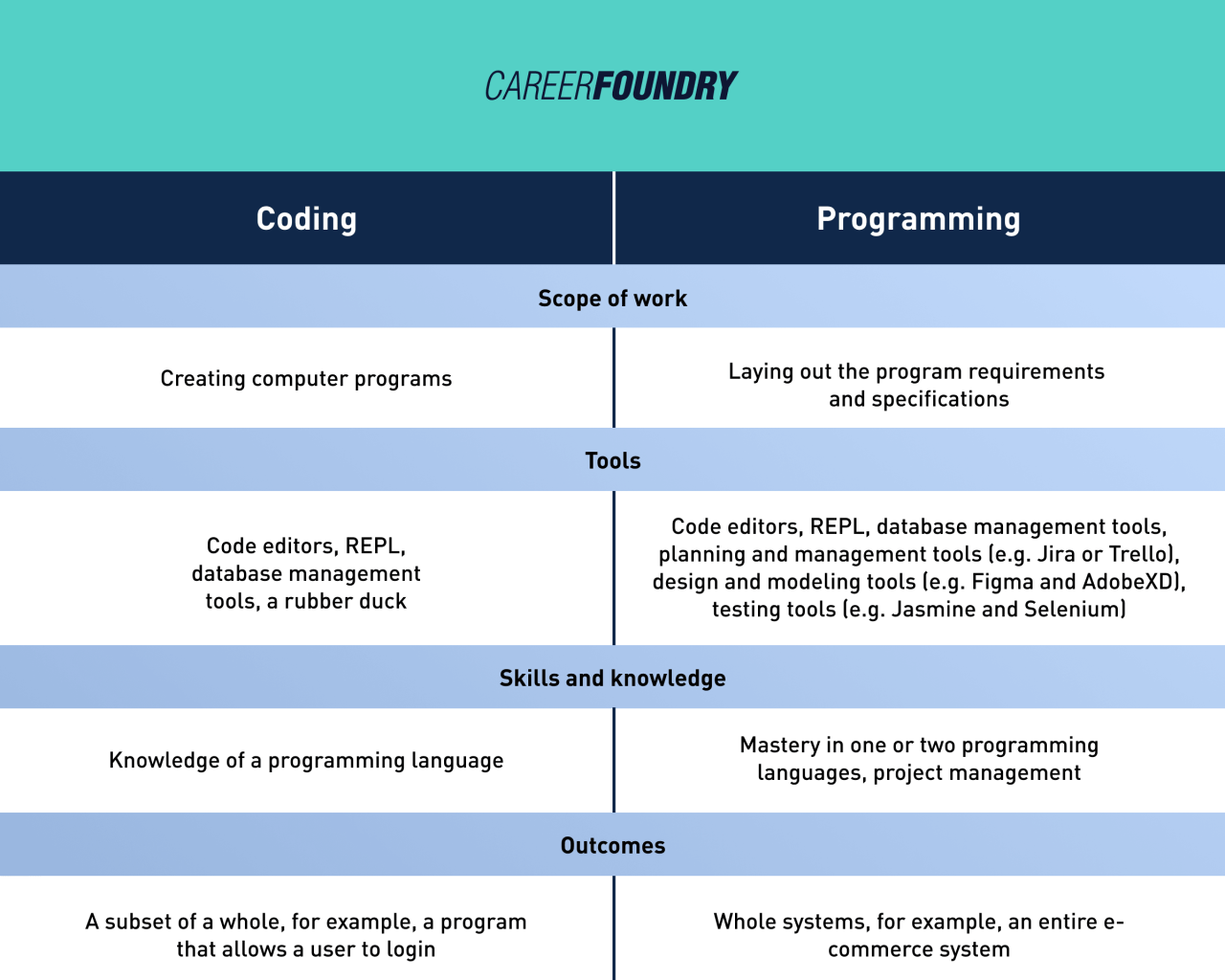
Comparison Table
The following table provides a comparative overview of the different types of load balancers:
| Feature | Hardware Load Balancer | Software Load Balancer | Cloud-Based Load Balancer |
|---|---|---|---|
| Performance | Highest | Moderate | High (Scalable) |
| Cost | Highest (Upfront) | Moderate | Variable (Pay-as-you-go) |
| Scalability | High (Requires Hardware) | Moderate (Hardware Dependent) | Automatic |
| Flexibility | Limited | High | Moderate |
| Management | Complex (Specialized Expertise) | Moderate | Simplified |
| Security Features | Advanced (DDoS, WAF) | Variable | Variable |
| Use Cases | High-traffic websites, complex networks, environments requiring advanced security. | Organizations with budget constraints, virtualized infrastructure, moderate traffic loads. | Organizations using cloud services, applications with fluctuating traffic, businesses seeking to reduce operational overhead. |
Common Load Balancing Algorithms
Load balancing algorithms are the core logic that determines how traffic is distributed across a group of backend servers. The choice of algorithm significantly impacts performance, resource utilization, and the overall resilience of the system. Understanding the characteristics of each algorithm is crucial for making informed decisions about which one best suits specific application needs. This section will explore several common load balancing algorithms and their operational mechanics.
Round Robin
The Round Robin algorithm is one of the simplest and most widely used load balancing methods. It distributes incoming requests sequentially to each server in the backend pool. This method treats all servers equally and is well-suited for scenarios where all servers have similar hardware specifications and processing capabilities.
- The load balancer cycles through the list of available servers.
- Each new request is sent to the next server in the list.
- Once the end of the list is reached, the process starts again from the beginning.
- If a server becomes unavailable, the load balancer skips it and continues to distribute traffic to the remaining active servers.
Least Connections
The Least Connections algorithm directs new requests to the server with the fewest active connections at any given time. This approach is designed to dynamically balance the load based on the current workload of each server, making it particularly useful in situations where server performance can vary or where requests have differing processing requirements.
- The load balancer tracks the number of active connections to each server.
- When a new request arrives, the load balancer selects the server with the fewest active connections.
- The request is then routed to that server.
- This process is repeated for each incoming request, continuously adjusting the distribution based on real-time connection counts.
IP Hash
The IP Hash algorithm uses the client’s IP address to determine which server should handle the request. This method ensures that a client’s requests are consistently directed to the same server, which can be beneficial for session persistence, where maintaining user sessions across multiple requests is critical.
- The client’s IP address is used as input to a hash function.
- The output of the hash function determines the server to which the request is sent.
- All requests from the same client IP address will consistently be directed to the same server, as long as the server remains available.
- If a server becomes unavailable, the hash function will redirect the client’s requests to a different server based on the computed hash.
Factors for Algorithm Selection
Selecting the appropriate load balancing algorithm involves careful consideration of several factors to ensure optimal performance and reliability. The characteristics of the application, the infrastructure, and the specific requirements of the service all play a role in this decision-making process.
- Application Type: Some applications benefit from session persistence, such as those using shopping carts or user logins. In such cases, IP Hash or a similar algorithm is often preferred to ensure that users are consistently directed to the same server.
- Server Capacity: If the servers have different hardware specifications or processing capabilities, the Least Connections algorithm can be more effective at distributing the load dynamically based on real-time server load.
- Traffic Patterns: For applications with relatively uniform request sizes and processing times, Round Robin may suffice. However, for applications with varying request complexities, Least Connections might be more appropriate.
- Session Persistence Requirements: If session persistence is not critical, Round Robin or Least Connections can be used. However, if maintaining user sessions is essential, IP Hash or cookie-based persistence is necessary.
- Server Health Monitoring: All load balancing algorithms should be coupled with robust server health monitoring to automatically detect and remove unhealthy servers from the pool. This ensures high availability and prevents requests from being sent to servers that cannot handle them.
Configuration Steps: Hardware Load Balancers

Configuring a hardware load balancer is a critical step in ensuring high availability and optimal performance for your applications. This process involves several key steps, from initial setup to ongoing monitoring and maintenance. This section will detail the process, providing practical guidance and examples to help you effectively configure a hardware load balancer.
Initial Setup and Configuration Process
The initial setup of a hardware load balancer involves physical installation, network configuration, and access to the management interface. Following these steps is crucial for a smooth deployment.
- Physical Installation: This step involves rack mounting the load balancer in your data center and connecting it to the power supply and network infrastructure. Ensure the load balancer is properly grounded and that the network cables are securely connected. The specific steps will vary depending on the hardware model, so refer to the vendor’s documentation for detailed instructions.
- Network Configuration: Configure the load balancer’s network interfaces with appropriate IP addresses, subnet masks, and gateway settings. This typically involves configuring at least two network interfaces: one for the management network and one or more for the data network that handles client traffic.
- Accessing the Management Interface: Hardware load balancers usually provide a web-based management interface, a command-line interface (CLI), or both. Access the management interface using the IP address assigned during network configuration. You’ll need to authenticate using the default or previously configured credentials.
- Basic Configuration: Configure basic settings such as the hostname, time zone, and network settings. This ensures the load balancer is properly identified on the network and that its internal clock is synchronized.
- Licensing: Activate the load balancer’s license, if required. Some hardware load balancers require a license to enable all features.
- Firmware Updates: Check for and apply any available firmware updates. Firmware updates often include security patches and performance improvements.
Configuring Health Checks to Monitor Server Availability
Health checks are essential for ensuring that the load balancer only directs traffic to healthy servers. These checks regularly probe the backend servers to determine their availability and responsiveness.
The following points detail how to configure health checks:
- Choose a Health Check Method: Select a suitable health check method based on your application’s requirements. Common methods include:
- TCP Health Checks: Verify basic TCP connectivity by establishing a connection to a specified port.
- HTTP/HTTPS Health Checks: Send HTTP/HTTPS requests to a specific URL and check for a successful response (e.g., HTTP 200 OK). This method allows for more in-depth checks, such as verifying the content of the response.
- ICMP Health Checks (Ping): Use ICMP echo requests (ping) to check server availability. This is a basic method that checks for network connectivity.
- Configure Health Check Parameters: Configure parameters such as the health check interval (how often the check is performed), the timeout (how long the load balancer waits for a response), and the number of retries (how many times the check is retried before a server is considered unhealthy).
- Specify the Health Check URL (for HTTP/HTTPS): If using HTTP/HTTPS health checks, specify the URL to be checked. This should be a page or endpoint that provides a reliable indication of the server’s health. For example, you might use a simple “health check” endpoint on your web server.
- Define Server Health Thresholds: Configure thresholds for marking a server as healthy or unhealthy. For instance, a server might be marked as unhealthy if it fails a certain number of consecutive health checks or if its response time exceeds a predefined threshold.
- Assign Health Checks to Server Pools: Associate the configured health checks with the server pools. The load balancer will use these health checks to monitor the health of the servers within each pool.
- Monitor Health Check Results: Regularly monitor the results of the health checks through the load balancer’s management interface. This allows you to identify and address any issues with server availability.
Sample Configuration for a Web Application
This sample configuration demonstrates how to set up a hardware load balancer for a basic web application, considering the assumption that the application runs on two backend servers.
The following is a simplified example of a configuration using a hypothetical hardware load balancer. The exact syntax and options will vary depending on the specific load balancer model.
- Define Server Pools: Create a server pool named “web-servers”.
- Add Backend Servers: Add the IP addresses and ports of the two backend web servers to the “web-servers” pool. For example:
- Server 1: 192.168.1.10:80
- Server 2: 192.168.1.11:80
- Configure Health Checks: Create an HTTP health check that checks the root URL (“/”). Configure the health check to use a 5-second timeout and a 10-second interval.
- Associate Health Checks with Server Pools: Associate the HTTP health check with the “web-servers” pool.
- Configure Virtual Server: Create a virtual server that listens on port 80 (HTTP) and forwards traffic to the “web-servers” pool. Configure the virtual server to use the IP address assigned to the load balancer.
- Configure Load Balancing Algorithm: Select a load balancing algorithm, such as Round Robin or Least Connections. Round Robin distributes traffic sequentially across the servers. Least Connections directs traffic to the server with the fewest active connections.
Configuration Steps
Software load balancers offer a flexible and cost-effective alternative to hardware solutions. They leverage readily available computing resources and can be deployed on virtual machines or physical servers. This section details the installation, configuration, and common practices for setting up software load balancers like HAProxy and Nginx.
Installing and Configuring a Software Load Balancer
The process of installing and configuring a software load balancer typically involves several key steps, which vary slightly depending on the specific software chosen and the operating system used. The general workflow is as follows:
- Installation: The first step is to install the chosen software load balancer. This is usually done through the operating system’s package manager. For example, on Debian/Ubuntu systems, you might use `apt-get install haproxy` or `apt-get install nginx`. On CentOS/RHEL systems, you’d use `yum install haproxy` or `yum install nginx`.
- Configuration File Modification: Once installed, the primary configuration file needs to be edited. The location of this file varies (e.g., `/etc/haproxy/haproxy.cfg` for HAProxy, `/etc/nginx/nginx.conf` for Nginx), and it dictates how the load balancer directs traffic.
- Defining Backends: Within the configuration file, the backend servers (the actual servers serving the application) are defined. This involves specifying their IP addresses or hostnames, along with optional parameters like port numbers and health check configurations.
- Configuring Frontend: The frontend configuration handles incoming client requests. It defines the ports the load balancer listens on, the protocols it supports (e.g., HTTP, HTTPS), and how it routes traffic to the defined backends.
- Choosing a Load Balancing Algorithm: Select a load balancing algorithm (e.g., round robin, least connections, IP hash) to distribute traffic among the backend servers.
- Testing the Configuration: After making changes, it’s crucial to test the configuration file for syntax errors. Both HAProxy and Nginx provide commands for this (e.g., `haproxy -c -f /etc/haproxy/haproxy.cfg` and `nginx -t`).
- Starting/Restarting the Load Balancer: Finally, start or restart the load balancer service to apply the new configuration. This usually involves using the system’s service management tools (e.g., `systemctl start haproxy`, `systemctl restart nginx`).
Common Configuration Directives Used in Software Load Balancers
Software load balancers utilize various configuration directives to control their behavior. Understanding these directives is key to effectively managing traffic distribution. The following are some common directives found in both HAProxy and Nginx configurations:
- listen/server (HAProxy) / upstream/server (Nginx): These directives define the backend servers and their associated settings. They specify the server’s address, port, and optional parameters such as weight (for traffic distribution), check (for health checks), and maxconn (maximum concurrent connections).
- bind (HAProxy) / listen (Nginx): This directive specifies the IP address and port that the load balancer will listen on for incoming client connections. It defines the frontend interface.
- balance (HAProxy) / upstream (Nginx): This directive defines the load balancing algorithm. Common options include `roundrobin`, `leastconn`, `ip_hash`, and `url_hash`.
- mode (HAProxy) / proxy_pass (Nginx): The `mode` directive in HAProxy specifies the protocol (e.g., `http`, `tcp`, `https`). In Nginx, `proxy_pass` is used to forward requests to the backend servers.
- timeout (HAProxy/Nginx): This directive sets various timeout values for connections, such as connection timeouts, client timeouts, and server timeouts.
- http-request/server-request (HAProxy) / location (Nginx): These directives allow for manipulating HTTP requests, such as adding or modifying headers, and defining rules for routing traffic based on URL paths or other criteria.
- option httpchk/health_check (HAProxy) / health_check (Nginx): These directives configure health checks to monitor the status of backend servers. If a server fails a health check, it is automatically removed from the load balancing pool.
Basic Configuration File Example for a Software Load Balancer
This example demonstrates a basic configuration for an HAProxy load balancer. It assumes two backend web servers and uses the round-robin algorithm.“`global log /dev/log local0 chroot /var/lib/haproxy user haproxy group haproxy daemondefaults log global mode http option httplog option dontlognull timeout connect 5s timeout client 50s timeout server 50sfrontend http-in bind
80 default_backend web-backendbackend web-backend balance roundrobin server web1 192.168.1.101:80 check server web2 192.168.1.102:80 check“`In this example:
- The `global` section sets global parameters, such as logging and security settings.
- The `defaults` section defines default settings that apply to all frontend and backend sections.
- The `frontend http-in` section configures the frontend, listening on port 80 and directing traffic to the `web-backend`.
- The `backend web-backend` section defines the backend servers. The `balance roundrobin` directive specifies the round-robin load balancing algorithm. The `server` directives define the backend servers, their IP addresses, and port numbers, and the `check` parameter enables health checks.
This is a basic example; more complex configurations can include SSL termination, header manipulation, and advanced health checks. The configuration file should be tailored to the specific needs of the application and the infrastructure. For Nginx, a similar configuration would be structured using `upstream` and `server` directives. The key is to understand the fundamental concepts and adapt the configuration to match the environment’s requirements.
Configuration Steps
Configuring cloud-based load balancers offers significant advantages in terms of scalability, ease of management, and cost-effectiveness. Cloud providers offer a variety of load balancing services that seamlessly integrate with other cloud resources, simplifying deployment and maintenance. These services often include features like automatic scaling, health checks, and SSL/TLS termination, streamlining the overall application delivery process.
Cloud-Based Load Balancer Setup
Setting up a load balancer on a cloud platform generally involves a few key steps, though the specific interface and options may vary slightly depending on the provider (AWS, Azure, Google Cloud, etc.). Understanding these steps provides a solid foundation for configuring and managing cloud-based load balancing solutions.To configure a cloud-based load balancer, you typically follow these steps:
- Select a Load Balancer Service: Identify the load balancing service offered by your cloud provider. For example, AWS offers Elastic Load Balancing (ELB), Azure provides Azure Load Balancer and Azure Application Gateway, and Google Cloud offers Cloud Load Balancing.
- Choose a Load Balancer Type: Decide on the type of load balancer that best suits your needs. Common types include:
- Application Load Balancers (Layer 7): Designed for HTTP/HTTPS traffic, offering advanced features like path-based routing and host-based routing.
- Network Load Balancers (Layer 4): Designed for TCP, UDP, and TLS traffic, offering high performance and low latency.
- Classic Load Balancers (AWS legacy): Provide basic load balancing functionality. (Note: These are often being phased out in favor of newer options.)
- Configure Listeners: Define listeners to accept incoming traffic. Listeners specify the protocol (HTTP, HTTPS, TCP, UDP) and port on which the load balancer will receive requests.
- Define Target Groups/Backend Pools: Specify the targets to which the load balancer will forward traffic. These targets are typically instances of your application (e.g., EC2 instances in AWS, Virtual Machines in Azure, or Compute Engine instances in Google Cloud). Configure health checks to monitor the health of these targets. The load balancer will only forward traffic to healthy targets.
- Configure Routing Rules (Application Load Balancers): For Application Load Balancers, define routing rules to direct traffic based on factors like the host name, path, or headers. This enables more sophisticated traffic management.
- Configure Security Groups/Firewall Rules: Set up security groups or firewall rules to control the inbound and outbound traffic to the load balancer and the backend instances. This is crucial for securing your application.
- Test and Monitor: After configuration, thoroughly test the load balancer to ensure it’s functioning correctly. Monitor its performance and health using the cloud provider’s monitoring tools.
SSL/TLS Termination Configuration
SSL/TLS termination is a critical security feature for load balancers, especially when handling HTTPS traffic. The load balancer decrypts the incoming encrypted traffic and forwards the unencrypted traffic to the backend servers. This process offloads the computationally intensive task of decryption from the backend servers, improving their performance.Configuring SSL/TLS termination typically involves the following steps:
- Obtain an SSL/TLS Certificate: You’ll need a valid SSL/TLS certificate. You can either upload your own certificate or use a certificate provided by your cloud provider (e.g., AWS Certificate Manager).
- Upload the Certificate to the Load Balancer: Upload the certificate and its associated private key to the load balancer service. The process varies by provider but usually involves navigating to the load balancer configuration settings.
- Configure a Secure Listener: Create a listener that listens for HTTPS traffic on port 443. Specify the SSL/TLS certificate to be used for decryption.
- Configure Security Policies: Choose an appropriate security policy to determine the supported SSL/TLS protocols and ciphers. Select a policy that balances security and compatibility. Modern policies are generally recommended for stronger security.
- Forward Unencrypted Traffic: The load balancer decrypts the HTTPS traffic and forwards the unencrypted HTTP traffic to the backend servers. Ensure the backend servers are configured to handle HTTP traffic on the appropriate port (usually port 80).
- Testing and Verification: Test the configuration by accessing your application through HTTPS. Verify that the connection is secure and that the load balancer is correctly decrypting and forwarding traffic.
Cloud Load Balancer Integration with Auto-Scaling
Integrating a cloud load balancer with an auto-scaling group is essential for achieving dynamic scalability. Auto-scaling automatically adjusts the number of backend instances based on traffic demand, ensuring your application can handle fluctuations in user load. The load balancer then distributes traffic across these dynamically scaling instances.The integration process generally involves these steps:
- Create an Auto-Scaling Group: Define an auto-scaling group that specifies the desired number of instances, the minimum and maximum number of instances, and the launch configuration (which defines the instance type, AMI, and other settings).
- Associate the Load Balancer with the Auto-Scaling Group: When creating or configuring the auto-scaling group, associate it with your load balancer. This ensures that new instances launched by the auto-scaling group are automatically registered with the load balancer.
- Configure Health Checks: Ensure that the load balancer’s health checks are correctly configured to monitor the health of the instances in the auto-scaling group. The auto-scaling group uses the load balancer’s health check status to determine whether to launch or terminate instances.
- Configure Scaling Policies: Define scaling policies that trigger the auto-scaling group to scale up or down based on metrics such as CPU utilization, network traffic, or custom metrics. For example, you might set a policy to add instances when CPU utilization exceeds a certain threshold.
- Testing and Monitoring: Test the auto-scaling functionality by simulating increased traffic. Verify that the auto-scaling group launches new instances and that the load balancer distributes traffic across them. Monitor the performance of the load balancer and the instances using the cloud provider’s monitoring tools.
Health Checks and Monitoring
Implementing robust health checks and comprehensive monitoring is crucial for maintaining the availability and performance of a load-balanced system. Health checks proactively identify unhealthy backend servers, preventing traffic from being routed to them, while monitoring provides valuable insights into the overall system’s health, performance, and potential bottlenecks. This ensures a seamless user experience and allows for proactive troubleshooting and optimization.
Importance of Health Checks in Load Balancing
Health checks are fundamental to the operational efficiency of load balancing. They are automated processes that regularly assess the health of backend servers. The load balancer uses the results of these checks to determine which servers are available to receive traffic. This dynamic approach ensures that only healthy servers participate in serving user requests, thereby minimizing downtime and improving overall application responsiveness.
Without health checks, a load balancer might continue to direct traffic to a failing server, resulting in service degradation or complete outages.
Health Check Methods
Different health check methods are available, each suited for different types of services and application architectures. Choosing the appropriate method depends on the specific requirements of the application and the level of detail needed to determine server health.
- HTTP Health Checks: These checks involve sending HTTP requests to a specific endpoint on the backend servers, such as a simple “ping” page or a status check URL. The load balancer monitors the HTTP response code (e.g., 200 OK, 503 Service Unavailable) and other metrics, like response time, to determine the server’s health. This is suitable for web applications and services that expose HTTP endpoints.
For example, a health check might send a GET request to
/health. A successful response (e.g., HTTP 200 OK) indicates the server is healthy. - TCP Health Checks: These checks establish a TCP connection to a specific port on the backend server. If the connection is successful, the server is considered healthy. This method is useful for checking the basic availability of services that use TCP, such as databases or custom applications.
For example, a TCP health check could attempt to connect to port 3306 on a database server.
- Custom Script Health Checks: These checks utilize custom scripts or programs to perform more complex health evaluations. These scripts can execute custom logic, query databases, or interact with other services to determine the server’s health. This provides the greatest flexibility and allows for tailored health checks based on the specific application’s requirements.
For instance, a custom script might check the CPU usage, memory utilization, and disk space of a server before determining its health.
- Database Health Checks: Specific health checks can target database servers. This may include checking database connection availability, verifying the ability to execute simple queries, or checking the replication status in a database cluster. This ensures that the database is accessible and functioning correctly.
For example, a database health check might attempt to connect to the database and execute a simple “SELECT 1” query.
Configuring Monitoring Tools
Monitoring tools are essential for tracking the performance and health of the load balancer and backend servers. They collect and analyze various metrics, providing insights into the system’s behavior and enabling proactive identification of issues. Effective monitoring involves configuring the monitoring tools to collect relevant data, visualize it effectively, and set up alerts for critical events.
- Metric Collection: Monitoring tools gather a variety of metrics, including:
- Load Balancer Metrics: Request rate, error rate, response times, connection counts, and resource utilization (CPU, memory, network).
- Backend Server Metrics: CPU usage, memory usage, disk I/O, network traffic, and application-specific metrics (e.g., database query times, queue lengths).
- Data Visualization: Most monitoring tools provide dashboards and graphs to visualize the collected metrics. This allows for easy identification of trends, anomalies, and potential performance bottlenecks. Dashboards should be customized to display the most relevant metrics for the specific application and infrastructure.
For example, a dashboard might display graphs of request rate, error rate, and response time for the load balancer, along with CPU usage and memory utilization for the backend servers. - Alerting and Notifications: Configure alerts to notify administrators when specific thresholds are exceeded or critical events occur. Alerts can be sent via email, SMS, or other notification channels. Proper alert configuration is critical for timely response to issues.
For instance, an alert could be triggered if the load balancer’s error rate exceeds a predefined threshold or if a backend server’s CPU usage remains consistently high. - Common Monitoring Tools: Several monitoring tools are available, including:
- Prometheus: An open-source monitoring and alerting toolkit.
- Grafana: A popular data visualization and dashboarding tool often used with Prometheus.
- Datadog: A cloud-based monitoring and analytics platform.
- New Relic: An application performance monitoring (APM) platform.
- Nagios: An open-source monitoring system.
Advanced Load Balancing Techniques
Load balancing, while powerful in its fundamental form, offers advanced techniques to optimize performance, enhance user experience, and improve application resilience. These techniques go beyond simple distribution of traffic and delve into more sophisticated strategies that cater to specific application needs and challenges. This section explores two key advanced load balancing techniques: session persistence and content-based routing.
Session Persistence (Sticky Sessions)
Session persistence, also known as sticky sessions, ensures that a user’s requests are consistently directed to the same backend server throughout their session. This is achieved by associating a unique identifier (e.g., a cookie) with the user’s session and using this identifier to route subsequent requests to the same server.Session persistence is a crucial technique for applications that rely on maintaining user state across multiple requests.
Consider the following points:
- How it works: The load balancer examines each incoming request for a session identifier. If a valid identifier is found, the request is routed to the server associated with that identifier. If no identifier is present, the load balancer selects a server based on its configured algorithm and associates the identifier with that server.
- Methods of implementation: Session persistence can be implemented using various methods, including:
- Cookie-based: The load balancer sets a cookie in the user’s browser containing the session identifier.
- URL rewriting: The load balancer modifies URLs to include the session identifier.
- SSL session ID: Leveraging the SSL session ID for persistence.
- Potential drawbacks: While session persistence offers benefits, it also introduces potential drawbacks:
- Reduced load balancing effectiveness: Stickiness can limit the even distribution of traffic if a particular server becomes overloaded.
- Server failures: If the server associated with a user’s session fails, the session is lost unless session data is replicated across servers.
- Scalability challenges: Managing a large number of sticky sessions can become complex in highly scalable environments.
Scenario Where Session Persistence is Necessary
Session persistence is essential in scenarios where user-specific data is stored on the backend server and needs to be accessed across multiple requests within a single session. Consider these common examples:
- E-commerce applications: Shopping carts often store user selections on a specific server. Without session persistence, a user’s items could be lost if requests are routed to different servers, disrupting the purchase process.
- Online banking: Secure banking sessions require session persistence to maintain a consistent connection to the server that handles user authentication and transaction processing. Redirecting to a different server mid-session could compromise security.
- Web applications with complex user profiles: Applications that store user preferences, settings, and personalized content on a specific server benefit from session persistence to ensure a consistent user experience.
For example, imagine a user browsing an e-commerce site. The user adds several items to their shopping cart. If session persistence is not enabled, each request to add an item or view the cart could be routed to a different server. This could lead to the cart contents being inconsistent or lost, frustrating the user and potentially leading to lost sales.
With session persistence, all requests from the user during that session are directed to the same server, ensuring the shopping cart data is consistently available.
Content-Based Routing in Load Balancing
Content-based routing is a sophisticated load balancing technique that directs traffic based on the content of the request itself. Instead of relying solely on factors like IP address or port, content-based routing examines the request headers, URLs, or other request attributes to make intelligent routing decisions.This method provides enhanced flexibility and control over traffic distribution, enabling more efficient resource utilization and improved application performance.
Consider these key aspects:
- How it works: The load balancer analyzes incoming requests based on predefined rules. These rules can be based on various criteria, including:
- URL paths: Directing requests to specific URLs to different backend servers.
- Request headers: Routing requests based on the “User-Agent” header (e.g., routing mobile traffic to a dedicated server).
- Content types: Directing requests for specific file types (e.g., images, videos) to optimized servers.
- Benefits of content-based routing:
- Improved application performance: Directing specific types of traffic to servers optimized for those types of requests.
- Enhanced security: Isolating sensitive applications or data on dedicated servers.
- Simplified application management: Decoupling different parts of an application and deploying them on different servers.
- Cost optimization: Efficiently utilizing resources by directing traffic to the most appropriate server.
- Examples of content-based routing:
- Routing traffic to different application versions: Directing users to different versions of an application based on their browser type or user agent.
- Serving static content from a CDN: Routing requests for static assets (images, CSS, JavaScript) to a Content Delivery Network (CDN) for faster delivery.
- Directing API requests to dedicated API servers: Separating API traffic from web traffic for improved performance and scalability.
For instance, consider a web application that serves both static content (images, videos) and dynamic content (web pages). Using content-based routing, the load balancer can direct requests for static content to a CDN or a dedicated server optimized for serving static assets, while directing requests for dynamic content to the application servers. This separation improves performance by reducing the load on the application servers and ensuring faster delivery of static content to users.
This type of routing is crucial in modern web architectures where efficiency and scalability are paramount.
Troubleshooting Common Issues

Troubleshooting is a critical aspect of load balancer management. Even with careful configuration, issues can arise. This section provides guidance on identifying, diagnosing, and resolving common problems encountered during load balancer operation. Effective troubleshooting ensures high availability and optimal performance of the application.
Server Unavailability
Server unavailability is a frequent issue that can disrupt service. Several factors can cause a server to become unavailable, and it is important to systematically identify the root cause.
- Identifying the Problem: The load balancer detects a server as unavailable when it fails health checks. Users may experience connection errors, slow response times, or complete service outages. Monitoring dashboards and logs are essential for detecting server unavailability.
- Troubleshooting Steps:
- Verify Server Status: Check the server’s status directly. Ensure the server is powered on, the operating system is running, and the application service is active. Use tools like `ping`, `traceroute`, or `telnet` to test network connectivity to the server.
- Examine Server Logs: Analyze server-side logs (e.g., application logs, system logs) for error messages or unusual activity. Look for signs of crashes, resource exhaustion (CPU, memory, disk), or network issues.
- Check Network Configuration: Ensure the server has the correct network configuration, including IP address, subnet mask, default gateway, and DNS settings. Verify that the server’s firewall rules allow traffic from the load balancer.
- Review Load Balancer Configuration: Confirm the load balancer’s configuration, including health check settings and server pool membership. Ensure the server is correctly configured within the load balancer.
- Test Health Checks: Manually test the health checks configured on the load balancer to determine if they are functioning correctly. This helps identify issues with the health check itself.
- Isolate the Problem: If possible, temporarily remove the problematic server from the load balancer pool and test it independently to rule out issues with the load balancer configuration.
- Example Scenario: A web server in a pool becomes unresponsive. The load balancer detects this through a failed HTTP health check (e.g., the server fails to respond to a GET request on the /health endpoint). The troubleshooting steps would involve checking the server’s status, examining its logs for errors, and verifying its network configuration. A common cause might be a service crash on the server or a resource bottleneck.
Traffic Distribution Problems
Inefficient traffic distribution can lead to performance bottlenecks and uneven resource utilization across servers. This can manifest as some servers being overloaded while others remain underutilized.
- Identifying the Problem: Symptoms of traffic distribution problems include slow response times for some users, high CPU or memory usage on specific servers, and inconsistent performance across the application. Monitoring tools provide insights into server resource utilization and traffic patterns.
- Troubleshooting Steps:
- Review Load Balancing Algorithm: Evaluate the configured load balancing algorithm. Ensure it is appropriate for the application and the server environment. For example, Round Robin might be suitable for equally powerful servers, while Least Connections might be better for handling varying server capacities.
- Check Server Weights: If using weighted load balancing, verify that the server weights are correctly configured to reflect the servers’ capacities. Incorrect weights can lead to uneven traffic distribution.
- Monitor Server Performance: Continuously monitor the CPU, memory, and disk I/O usage of each server in the pool. Identify servers that are consistently overloaded or underutilized.
- Analyze Traffic Patterns: Examine traffic patterns using monitoring tools. Determine if certain requests are disproportionately affecting specific servers. This can help identify issues with the application’s logic or data access patterns.
- Inspect Session Persistence: If session persistence is enabled, ensure it is configured correctly. Misconfigured session persistence can lead to uneven traffic distribution if users are consistently routed to the same server.
- Consider Sticky Sessions: For applications requiring session persistence, consider using sticky sessions (e.g., cookie-based persistence). However, be aware that sticky sessions can limit the benefits of load balancing if not implemented carefully.
- Example Scenario: A web application uses Round Robin load balancing, but one server consistently experiences higher CPU usage than others. This suggests a traffic distribution problem. Troubleshooting might involve examining the application logs on each server to determine if certain requests are causing the load imbalance, and then potentially adjusting the load balancing algorithm or server weights.
Health Check Failures
Health checks are essential for ensuring that the load balancer only routes traffic to healthy servers. Health check failures can indicate underlying issues with the servers or the health check configuration itself.
- Identifying the Problem: Health check failures are indicated by the load balancer marking a server as unavailable. This results in users being unable to access the application or experiencing degraded performance.
- Troubleshooting Steps:
- Verify Health Check Configuration: Review the health check configuration on the load balancer. Ensure the health check type (e.g., HTTP, TCP, ICMP) and parameters (e.g., interval, timeout, retries) are appropriate for the application and the server environment.
- Test Health Checks Manually: Manually test the health checks from the load balancer to verify they are functioning correctly. Use tools like `curl` or `telnet` to simulate the health check requests.
- Examine Server Logs: Analyze server-side logs for error messages related to the health check requests. Look for signs of application crashes, resource exhaustion, or network issues.
- Check Server Availability: Ensure the application service being checked by the health check is running and accessible on the server.
- Adjust Health Check Parameters: If health check failures are intermittent, consider adjusting the health check parameters (e.g., increasing the timeout or the number of retries) to reduce false positives. However, be cautious, as excessively relaxed health checks can lead to traffic being routed to unhealthy servers.
- Review Network Connectivity: Verify that the load balancer has network connectivity to the servers and that there are no firewall rules blocking the health check requests.
- Example Scenario: An HTTP health check fails for a web server. Troubleshooting would involve verifying the health check configuration, manually testing the health check using `curl`, examining the web server’s logs for errors, and ensuring the web server is running and accessible. A common cause might be a misconfigured health check URL or a server-side error.
Use of Logging and Monitoring Tools
Effective use of logging and monitoring tools is critical for diagnosing and resolving load balancing issues. These tools provide valuable insights into the performance and health of the load balancer and the backend servers.
- Logging:
- Purpose: Logging captures events, errors, and other information about the load balancer’s operation and the traffic it handles. Logs are essential for identifying the root cause of problems.
- Tools: Common logging tools include system logs (e.g., syslog), application logs, and specialized load balancer logs.
- Best Practices:
- Enable detailed logging for all relevant events.
- Configure log rotation to manage log file size.
- Centralize logs for easier analysis.
- Regularly review logs for errors and warnings.
- Monitoring:
- Purpose: Monitoring provides real-time insights into the performance and health of the load balancer and the backend servers. Monitoring dashboards provide a visual representation of key metrics.
- Tools: Common monitoring tools include the load balancer’s built-in monitoring features, third-party monitoring tools (e.g., Prometheus, Grafana, Nagios, Zabbix), and cloud-based monitoring services (e.g., AWS CloudWatch, Azure Monitor, Google Cloud Monitoring).
- Key Metrics: Monitor key metrics such as:
- Traffic Volume: Requests per second, bytes per second.
- Response Times: Average response time, 95th percentile response time.
- Error Rates: HTTP error codes (e.g., 500, 503).
- Server Resource Utilization: CPU usage, memory usage, disk I/O.
- Health Check Status: Server availability.
- Best Practices:
- Configure alerts for critical metrics.
- Establish baseline performance metrics.
- Regularly review monitoring dashboards.
- Use monitoring data to identify performance bottlenecks and trends.
- Correlation: Correlating data from logs and monitoring tools is crucial for effective troubleshooting. This involves linking events and metrics to identify the root cause of problems. For example, an increase in HTTP 500 errors in the logs might correlate with a spike in CPU usage on a backend server, indicating a potential performance issue.
- Example Scenario: A monitoring dashboard shows a sudden increase in average response times. Examining the load balancer logs reveals a surge in HTTP 503 errors. Further investigation reveals that one of the backend servers is experiencing high CPU usage. This information, correlated, points to a server overload problem.
Security Considerations
Load balancers are critical components of modern infrastructure, and securing them is paramount to protecting applications and data. A compromised load balancer can expose the entire backend to various threats, leading to data breaches, service disruptions, and reputational damage. Implementing robust security measures at the load balancing layer is essential for maintaining the integrity, availability, and confidentiality of services.
Security Best Practices for Load Balancer Configuration
Implementing security best practices for load balancer configuration involves a multi-layered approach, encompassing access control, regular updates, and proactive monitoring. This helps to reduce the attack surface and mitigate potential risks.
- Access Control: Implement strict access controls to restrict who can manage and configure the load balancer. Use strong passwords, multi-factor authentication (MFA), and role-based access control (RBAC) to limit access to authorized personnel only. Regularly review and update access permissions to reflect changes in personnel or responsibilities.
- Regular Updates and Patching: Keep the load balancer’s firmware, software, and operating system up-to-date with the latest security patches. Vulnerabilities are frequently discovered, and timely patching is crucial to address known exploits. Automate the patching process whenever possible to ensure consistent and timely updates.
- Network Segmentation: Isolate the load balancer within a secure network segment, separate from the public internet and other critical infrastructure components. This limits the impact of a potential compromise by containing the blast radius. Use firewalls and intrusion detection systems (IDS) to monitor and control network traffic.
- Secure Configuration: Follow the vendor’s security hardening guidelines and disable unnecessary features and services. Review and configure security settings such as logging, auditing, and encryption. Regularly audit the configuration to identify and address any deviations from the established security baseline.
- Monitoring and Alerting: Implement comprehensive monitoring and alerting systems to detect suspicious activity, performance issues, and security breaches. Monitor logs for unusual access attempts, configuration changes, and other indicators of compromise. Configure alerts to notify the appropriate personnel of any security incidents promptly.
- Web Application Firewall (WAF) Integration: Integrate a WAF with the load balancer to provide additional protection against web-based attacks, such as cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF). The WAF can inspect and filter malicious traffic before it reaches the backend servers.
- Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities and weaknesses in the load balancer configuration. This helps to proactively identify and address potential security risks before they can be exploited.
Implementation of SSL/TLS Encryption
SSL/TLS encryption is essential for securing communication between clients and the load balancer, as well as between the load balancer and backend servers. It protects sensitive data in transit from eavesdropping and tampering.
- SSL/TLS Termination: Configure the load balancer to terminate SSL/TLS connections. This means the load balancer decrypts the incoming traffic and forwards it to the backend servers in plain text (or, optionally, encrypts it again). This offloads the SSL/TLS processing from the backend servers, improving their performance.
- Certificate Management: Obtain and install SSL/TLS certificates from a trusted Certificate Authority (CA) on the load balancer. Ensure the certificates are valid and up-to-date to avoid browser warnings and security vulnerabilities. Implement a process for renewing certificates before they expire.
- Cipher Suite Configuration: Configure the load balancer to use strong and secure cipher suites. Avoid using outdated or weak cipher suites that are vulnerable to known attacks. Regularly review and update the cipher suite configuration to address newly discovered vulnerabilities.
- Perfect Forward Secrecy (PFS): Enable Perfect Forward Secrecy (PFS) to ensure that even if the private key of the load balancer is compromised, past communications remain secure. This is achieved by using ephemeral keys for each session.
- SSL/TLS Versions: Disable support for older, insecure SSL/TLS versions (SSLv3, TLS 1.0, and TLS 1.1). Only support the latest and most secure versions (TLS 1.2 and TLS 1.3) to mitigate known vulnerabilities.
- Backend Encryption (Optional): Consider encrypting the traffic between the load balancer and the backend servers, especially if the communication traverses an untrusted network. This adds an extra layer of security and protects against potential eavesdropping.
Guidelines for Protecting Load Balancers Against DDoS Attacks
Load balancers are often a primary target for Distributed Denial of Service (DDoS) attacks, which aim to overwhelm the system and make it unavailable. Implementing effective DDoS protection measures is critical for maintaining service availability.
- Rate Limiting: Configure rate limiting to restrict the number of requests from a single IP address or source. This helps to mitigate volumetric attacks by limiting the amount of traffic that can be directed at the backend servers.
- Connection Limiting: Limit the number of concurrent connections from a single IP address. This prevents attackers from establishing a large number of connections to consume resources.
- SYN Flood Protection: Implement SYN flood protection to mitigate SYN flood attacks, which attempt to exhaust server resources by sending a large number of incomplete TCP connection requests. Techniques include SYN cookies, SYN cache, and connection tracking.
- Web Application Firewall (WAF) Integration: Integrate a WAF with the load balancer to provide advanced DDoS protection capabilities. WAFs can detect and filter malicious traffic, including HTTP floods and application-layer attacks.
- Blacklisting and Whitelisting: Implement IP address blacklisting and whitelisting to block traffic from known malicious sources and allow traffic only from trusted sources. This can be used to filter out botnet traffic and other unwanted requests.
- Anycast and Geolocation-Based Routing: Consider using Anycast routing to distribute traffic across multiple load balancer instances geographically. This increases the capacity to absorb DDoS attacks and improves resilience. Geolocation-based routing can be used to direct traffic to the closest available load balancer instance.
- Traffic Scrubbing Services: Utilize a traffic scrubbing service to filter out malicious traffic before it reaches the load balancer. These services typically operate at the network layer and can handle large-scale DDoS attacks.
- Monitoring and Alerting: Implement comprehensive monitoring and alerting to detect and respond to DDoS attacks promptly. Monitor traffic patterns, request rates, and error rates to identify unusual activity. Configure alerts to notify the appropriate personnel of any potential DDoS attacks.
Closing Summary
In conclusion, mastering load balancer configuration is paramount for building high-performing, scalable, and reliable web applications. This guide has equipped you with the knowledge and tools to navigate the landscape of load balancing, from understanding the core concepts to implementing advanced techniques. By applying the principles discussed, you can ensure your applications remain accessible and responsive, even under heavy load.
Embrace the power of load balancing and elevate your web development skills to new heights.