Embark on a journey into the future of democracy with “How to Coding Blockchain Voting System,” a comprehensive exploration of how blockchain technology can revolutionize the way we vote. This guide delves into the core principles of blockchain, explaining how its inherent security, transparency, and immutability can address the vulnerabilities of traditional voting systems.
From understanding the foundational concepts to crafting secure smart contracts and deploying a functional voting platform, we’ll navigate the intricacies of building a blockchain-based voting system. This will include detailed discussions on system architecture, user authentication, security considerations, and best practices for a robust and reliable voting experience. We will also explore the legal and regulatory landscape, offering insights into the future of blockchain voting.
Introduction to Blockchain Voting Systems
Blockchain technology is revolutionizing numerous sectors, and its application in voting systems offers a compelling alternative to traditional methods. This approach leverages the inherent properties of blockchain, such as immutability, transparency, and security, to address the vulnerabilities and limitations of conventional voting processes. The integration of blockchain in voting aims to create a more trustworthy, efficient, and accessible system for citizens to participate in democratic processes.
Fundamental Concepts of Blockchain in Voting
Blockchain technology provides a decentralized, distributed, and immutable ledger for recording transactions, making it an ideal solution for voting systems. In a blockchain voting system, each vote cast is recorded as a transaction and added to a block. This block is then cryptographically linked to the previous block, forming a chain. This structure ensures that the data cannot be altered or tampered with, as any attempt to modify a vote would require changing all subsequent blocks in the chain, which is computationally infeasible.Key concepts include:
- Decentralization: The voting data is distributed across a network of computers, eliminating a single point of failure and reducing the risk of manipulation.
- Immutability: Once a vote is recorded on the blockchain, it cannot be changed, ensuring the integrity of the election results.
- Transparency: The voting process is open and auditable, allowing voters to verify that their votes have been correctly recorded and counted (subject to privacy considerations).
- Security: Cryptographic techniques are used to secure the voting data, protecting against fraud and unauthorized access.
- Smart Contracts: Automated execution of voting rules and processes, reducing the need for human intervention and potential errors.
Comparative Analysis: Traditional Voting Systems vs. Blockchain-Based Voting Systems
Traditional voting systems often face challenges such as voter fraud, lack of transparency, and high costs. Blockchain-based voting systems offer a potential solution to these issues.
| Feature | Traditional Voting Systems | Blockchain-Based Voting Systems | Advantages & Disadvantages |
|---|---|---|---|
| Security | Vulnerable to fraud, manipulation, and hacking. Can be susceptible to insider threats and human error. | Highly secure due to cryptographic techniques and immutability. Reduces the risk of fraud and manipulation. | Advantages: Enhanced security, reduced fraud risk. Disadvantages: Potential for vulnerabilities in smart contracts and key management. Requires robust security audits. |
| Transparency | Often opaque, with limited auditability. Can be difficult for voters to verify the accuracy of the results. | Highly transparent and auditable. Voters can verify that their votes have been correctly recorded and counted (subject to privacy considerations). | Advantages: Increased transparency, enhanced auditability. Disadvantages: Requires careful management of voter privacy and data protection. |
| Cost | Can be expensive due to the need for physical infrastructure, manual processes, and election officials. | Potentially lower costs due to automation, reduced need for physical infrastructure, and streamlined processes. | Advantages: Potential for cost savings through automation. Disadvantages: Initial setup costs for blockchain infrastructure and potential for ongoing maintenance expenses. |
| Accessibility | Can be geographically limited, requiring voters to travel to polling stations. May exclude voters with disabilities or those living abroad. | Potentially more accessible, allowing for remote voting via internet-connected devices. Can improve voter turnout. | Advantages: Increased accessibility, improved voter turnout. Disadvantages: Requires reliable internet access and digital literacy. Raises concerns about voter authentication and identity verification. |
Benefits of Using Blockchain for Voting
Blockchain technology offers several key benefits when applied to voting systems, leading to more secure, transparent, and efficient electoral processes. These advantages can significantly improve voter confidence and the overall integrity of democratic elections.
- Enhanced Security: Blockchain’s cryptographic properties and distributed ledger technology make it extremely difficult to tamper with or manipulate votes. The immutability of the blockchain ensures that once a vote is recorded, it cannot be altered.
- Increased Transparency: Blockchain-based voting systems provide a transparent and auditable record of all votes cast. Voters can potentially track their votes and verify that they have been correctly recorded. This transparency fosters trust in the electoral process.
- Improved Auditability: The transparent and immutable nature of blockchain allows for comprehensive audits of the voting process. Auditors can easily verify the accuracy of the results and identify any potential discrepancies.
- Reduced Costs: Blockchain can automate many aspects of the voting process, such as voter registration, vote counting, and result reporting. This automation can lead to significant cost savings compared to traditional voting systems.
- Enhanced Efficiency: Blockchain-based voting systems can streamline the voting process, making it faster and more efficient. This can lead to higher voter turnout and quicker results.
Core Components of a Blockchain Voting System
Blockchain voting systems, while complex in their underlying technology, are built upon a few essential components. These components work in concert to provide a secure, transparent, and auditable voting process. Understanding these core elements is crucial to grasping how these systems function and the advantages they offer over traditional voting methods.
Smart Contracts in Voting
Smart contracts are at the heart of blockchain voting systems. They automate the voting process, ensuring that votes are recorded accurately and that the rules of the election are followed without the need for intermediaries.Smart contracts function through the following key aspects:
- Automated Vote Recording: Smart contracts record votes directly on the blockchain, creating an immutable record of each vote. This eliminates the possibility of tampering or manipulation.
- Rule Enforcement: Smart contracts enforce the rules of the election, such as voter eligibility, vote limits, and the timing of the election. These rules are pre-programmed into the contract and automatically applied.
- Transparency and Auditability: Because all actions are recorded on the blockchain, the entire voting process is transparent and auditable. Anyone can view the votes and verify the results, enhancing trust in the system.
- Self-Execution: Smart contracts execute automatically when predefined conditions are met. For example, the contract can automatically tally votes at the end of the voting period and announce the results.
Smart contracts also ensure the integrity of the voting process. For example, the smart contract might include a mechanism to prevent double-voting, ensuring each eligible voter casts only one vote. This could involve unique identifiers or cryptographic techniques.
Decentralized Storage Options for Voting Data
Decentralized storage is crucial for storing voting data in a blockchain voting system. It ensures data is distributed across multiple nodes, making it resistant to censorship and single points of failure. Several options exist, each with its own strengths and weaknesses.Different decentralized storage options are used for voting data:
- Blockchain Native Storage: Voting data can be stored directly on the blockchain itself. This provides the highest level of security and immutability, as all data is part of the blockchain’s consensus mechanism. However, it can be more expensive and slower due to the need to write data to every node.
- Strengths: High security, immutability, transparency.
- Weaknesses: High cost, slower transaction speeds, scalability limitations.
- InterPlanetary File System (IPFS): IPFS is a peer-to-peer distributed file system that allows for storing and retrieving data in a decentralized manner. Voting data, such as ballot images or voter registration information, can be stored on IPFS, with only a hash of the data stored on the blockchain.
- Strengths: Cost-effective, scalable, good for storing large files.
- Weaknesses: Data is not inherently immutable (unless combined with other mechanisms), requires a separate infrastructure.
- Other Decentralized Storage Solutions: Other options, such as Swarm or Filecoin, also offer decentralized storage solutions, each with its own features and trade-offs. These alternatives often provide similar benefits to IPFS but may offer different performance characteristics or economic models.
- Strengths: Varies depending on the specific solution, often focusing on scalability or cost-effectiveness.
- Weaknesses: Requires research and understanding of the specific storage solution and its limitations.
The choice of storage solution depends on the specific needs of the voting system. For example, if immutability and security are paramount, storing data directly on the blockchain might be preferred, even if it is more expensive. If scalability and cost-effectiveness are more important, solutions like IPFS might be more appropriate.
Designing the Voting Process
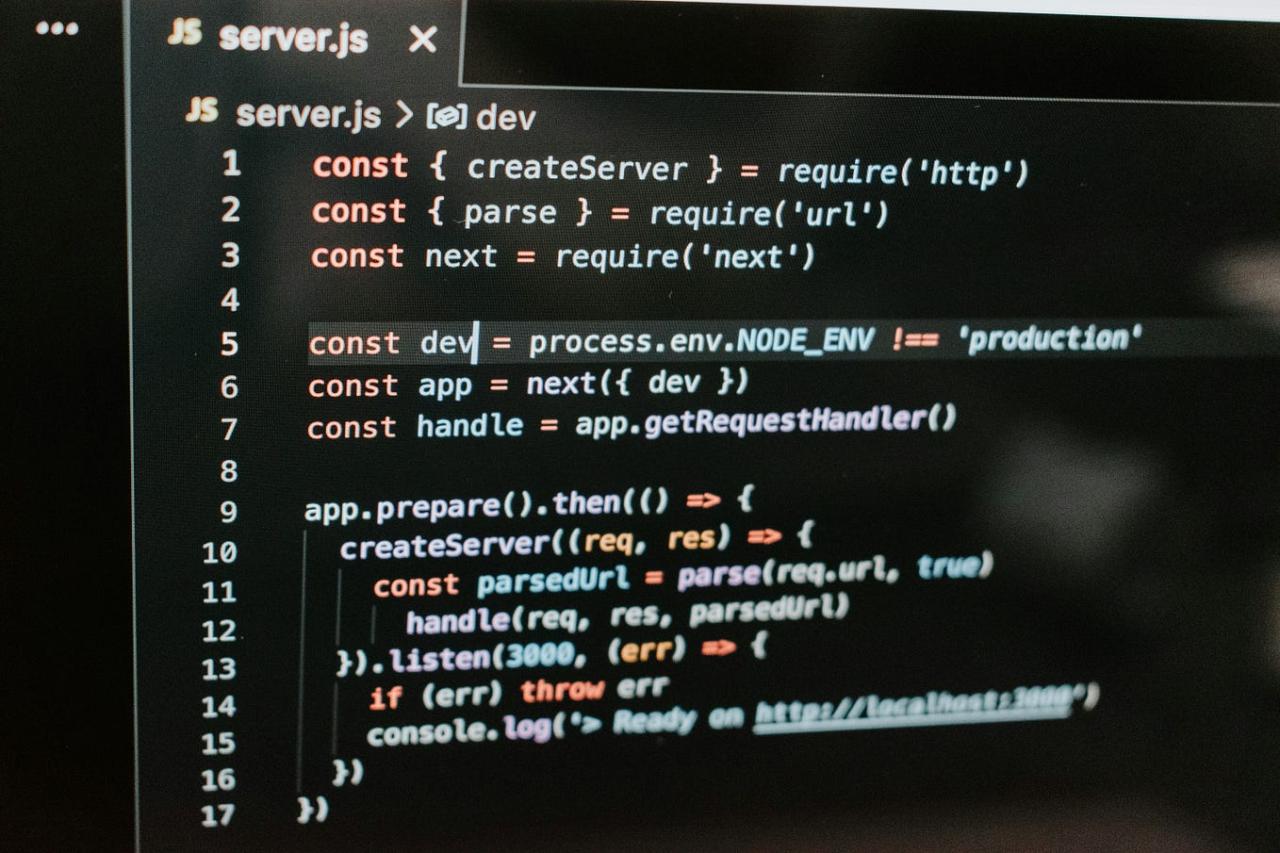
The design of the voting process is crucial for the success of a blockchain-based voting system. It must balance security, transparency, and usability to ensure voter confidence and participation. This section Artikels the critical steps involved in designing a secure and efficient voting process, from voter authentication to vote counting.
User Authentication and Registration Process for Voters
A robust authentication and registration process is the first line of defense against fraudulent voting. It must verify the identity of each voter while ensuring the privacy of their personal information.
- Identity Verification: This involves confirming the voter’s eligibility. The process typically includes verifying voter identity against a trusted source, such as a government-issued ID database or a national voter registry. This can be achieved through several methods, including:
- KYC/AML Compliance: Implement “Know Your Customer” (KYC) and Anti-Money Laundering (AML) procedures to verify voter identities. This might involve scanning government-issued IDs and matching them against a database.
- Decentralized Identifiers (DIDs): Utilize DIDs to allow voters to control their identity information. DIDs are globally unique identifiers that allow individuals to prove their identity without revealing personal information.
- Secure Registration: The registration process should be secure to prevent unauthorized access and data breaches.
- Multi-Factor Authentication (MFA): Implement MFA, such as requiring a password and a one-time code sent to a registered email or phone number, to enhance security.
- Data Encryption: Encrypt all voter data, both in transit and at rest, to protect against unauthorized access. Use strong encryption algorithms, such as AES-256.
- User-Friendly Interface: The registration process should be easy to navigate and understand.
- Clear Instructions: Provide clear and concise instructions for each step of the registration process.
- Responsive Design: Ensure the registration process is accessible on various devices, including desktops, tablets, and smartphones.
Casting a Vote on the Blockchain
Casting a vote on the blockchain involves several steps, each designed to ensure the vote’s integrity and immutability. These steps must be executed securely and transparently.
- Voter Authentication: The voter authenticates themselves using their registered credentials (e.g., username/password and MFA).
- Ballot Selection: The voter selects their choices from the available candidates or options presented on the ballot.
- Transaction Creation: A transaction is created containing the voter’s choices, encrypted to protect privacy. The voter’s public key is used to encrypt the vote, and only the voter can decrypt it later if needed for verification.
- Transaction Signing: The voter digitally signs the transaction using their private key. This proves the vote’s authenticity and prevents tampering.
- Transaction Submission: The signed transaction is submitted to the blockchain network.
- Vote Confirmation: The blockchain network validates the transaction and includes it in a block. Once the block is confirmed, the vote is recorded on the blockchain.
Flow Diagram of the Voting Process
The following flow diagram illustrates the entire voting process, from voter registration to vote counting. The diagram shows the sequence of actions and interactions between the voter, the voting system, and the blockchain.
Voter Registration Phase:
Step 1: Voter initiates registration.
Step 2: System verifies voter eligibility using identity verification methods.
Step 3: System generates unique voter ID and stores encrypted voter data.
Step 4: Voter receives confirmation and login credentials.
Voting Phase:
Step 1: Voter logs in securely with credentials.
Step 2: System presents the ballot.
Step 3: Voter selects choices.
Step 4: System encrypts the vote and creates a transaction.
Step 5: Voter signs the transaction with a private key.
Step 6: Transaction submitted to the blockchain.
Step 7: Blockchain validates and confirms the transaction.
Step 8: Vote recorded on the blockchain.
Vote Counting Phase:
Step 1: System decrypts the votes (or aggregates encrypted votes for tallying).
Step 2: System counts the votes.
Step 3: System publishes the results.
Key elements of the diagram:
- Voter: Represents the individual participating in the election.
- Voting System: The software and hardware infrastructure that facilitates the voting process.
- Blockchain: The distributed ledger that records and stores the votes.
- Arrows: Indicate the flow of actions and data between the components.
Smart Contract Development for Voting

Smart contracts are the backbone of a blockchain voting system, automating the voting process and ensuring transparency and immutability. They are self-executing contracts written in code and deployed on a blockchain. These contracts define the rules of the voting process, manage voter registration, record votes, tally results, and enforce the security measures. This section will explore the critical aspects of developing smart contracts for voting systems.
Core Functions of a Smart Contract for Voting
A voting smart contract must perform several core functions to facilitate a secure and reliable voting process. These functions work together to ensure that votes are accurately recorded, the results are tallied correctly, and the integrity of the election is maintained. The key functionalities are:
- Vote Recording: This is the primary function, where each vote is securely recorded on the blockchain. It involves accepting votes from registered voters and storing them in a way that prevents tampering and maintains voter anonymity. The vote recording function needs to verify the voter’s identity, ensuring only eligible voters can participate.
- Result Tallying: The smart contract must automatically tally the votes once the voting period has ended. This function aggregates the recorded votes and calculates the outcome of the election. This process is transparent and verifiable, as anyone can view the tallying process on the blockchain.
- Vote Verification: The smart contract should provide mechanisms to verify the validity of each vote. This ensures that votes are cast by eligible voters and that they haven’t been altered. Vote verification can involve checking voter eligibility, ensuring the vote is cast within the voting period, and confirming the vote’s integrity.
Code Snippets for Smart Contract Development (Solidity)
Solidity is a popular programming language for writing smart contracts on the Ethereum blockchain. Here are some code snippets illustrating key functionalities. Note: These are simplified examples and not production-ready code.
Voter Registration (Illustrative):
pragma solidity ^0.8.0; contract Voting mapping (address => bool) public voters; function registerVoter(address _voter) public require(!voters[_voter], "Voter already registered."); voters[_voter] = true;
This snippet shows a basic voter registration process. The `voters` mapping stores the addresses of registered voters.
The `registerVoter` function adds a new voter’s address to the mapping. The `require` statement checks to ensure the voter is not already registered.
Vote Casting (Illustrative):
pragma solidity ^0.8.0; contract Voting mapping (address => bool) public voters; mapping (uint => uint) public votes; // Option ID to vote count uint public totalVotes; function vote(uint _option) public require(voters[msg.sender], "You are not a registered voter."); require(_option > 0 && _option <= 3, "Invalid option."); // Assuming 3 options votes[_option]++; totalVotes++;
This example demonstrates vote casting.
The `vote` function allows a registered voter (`msg.sender`) to cast a vote for a specific option (`_option`). The `require` statements check for voter registration and the validity of the option selected. The vote count for the chosen option is incremented, and the `totalVotes` counter is updated.
Result Tallying (Illustrative):
pragma solidity ^0.8.0; contract Voting // ... (previous code) ... function getResult(uint _option) public view returns (uint) return votes[_option]; function getTotalVotes() public view returns (uint) return totalVotes;
This snippet shows functions for retrieving the results.
The `getResult` function allows anyone to view the vote count for a specific option. The `getTotalVotes` function returns the total number of votes cast.
Handling Potential Security Vulnerabilities
Smart contracts are immutable, meaning that once deployed, they cannot be easily changed. Therefore, it's crucial to address security vulnerabilities during the development phase. Several potential vulnerabilities must be considered:
- Reentrancy Attacks: A malicious contract could recursively call the voting contract before the first call is completed, potentially draining funds or manipulating votes. Mitigations include using the `Checks-Effects-Interactions` pattern, reentrancy guards (using modifiers like `nonReentrant`), and careful consideration of external calls.
- Integer Overflow/Underflow: Older versions of Solidity were susceptible to integer overflows and underflows, which could lead to incorrect vote counts. Modern Solidity versions (0.8.0 and later) have built-in checks to prevent this.
- Denial-of-Service (DoS) Attacks: Malicious actors could attempt to flood the contract with transactions, preventing legitimate users from casting their votes. Implementing rate limiting, gas limits, and other defensive measures can mitigate this.
- Front-Running: In some cases, users might be able to observe pending transactions and attempt to manipulate the voting process by submitting their transactions with higher gas fees to get them processed first. Techniques such as using commit-reveal schemes can prevent this.
- Voter Identity Verification: Ensuring only eligible voters participate is critical. Solutions include using whitelists, identity management systems, and off-chain verification mechanisms to prevent unauthorized voting.
By understanding and mitigating these vulnerabilities, developers can build secure and reliable smart contracts for blockchain-based voting systems.
Security Considerations and Best Practices
Blockchain voting systems, while offering significant advantages in terms of transparency and immutability, are not inherently invulnerable. Securing these systems is paramount to ensure the integrity of the voting process and maintain public trust. This section explores potential security threats, mitigation strategies, and best practices for developing robust and secure blockchain-based voting solutions.
Potential Security Threats
Blockchain voting systems face a variety of security threats that can compromise the voting process. Understanding these threats is the first step towards developing effective countermeasures.
- Double-Spending: This threat involves a voter attempting to cast multiple votes, effectively manipulating the election results. This can be achieved by exploiting vulnerabilities in the voting system or the underlying blockchain.
- Sybil Attacks: In a Sybil attack, an attacker creates numerous fake identities (Sybil nodes) to control a significant portion of the voting power. This allows the attacker to influence the outcome of the election by casting a disproportionate number of votes.
- Denial-of-Service (DoS) Attacks: DoS attacks aim to disrupt the voting process by overwhelming the network with traffic, making it unavailable to legitimate voters. Distributed Denial-of-Service (DDoS) attacks, where the attack originates from multiple sources, are particularly challenging to defend against.
- 51% Attacks: If an attacker controls more than 50% of the network's computational power (e.g., mining power in Proof-of-Work blockchains), they can potentially manipulate the blockchain, including reversing transactions (votes) or censoring certain voters.
- Malicious Smart Contracts: Vulnerabilities in the smart contract code itself can be exploited to manipulate the voting process. This includes bugs that allow for unauthorized access, vote manipulation, or the theft of funds.
- Key Management Issues: Compromised private keys can lead to unauthorized access and vote manipulation. Poor key management practices are a significant security risk.
- Data Breaches: Although blockchain data is immutable, voter information stored off-chain (e.g., voter registration data) is vulnerable to breaches, potentially exposing sensitive personal information.
Mitigation Strategies
Addressing the security threats requires a multi-layered approach, combining cryptographic techniques, robust consensus mechanisms, and rigorous auditing procedures.
- Cryptographic Techniques:
- Encryption: Voter identities and votes should be encrypted to protect confidentiality. Encryption algorithms like AES (Advanced Encryption Standard) and RSA (Rivest–Shamir–Adleman) can be employed.
- Digital Signatures: Digital signatures ensure the authenticity and non-repudiation of votes. Voters digitally sign their votes using their private keys.
- Hashing: Hashing algorithms (e.g., SHA-256) are used to generate unique fingerprints of votes, ensuring their integrity.
- Consensus Mechanisms:
- Proof-of-Work (PoW): While PoW (used by Bitcoin) is effective against double-spending, it can be susceptible to 51% attacks. It requires a significant amount of computational power to control the network.
- Proof-of-Stake (PoS): PoS systems (used by Ethereum and others) make it more difficult for attackers to gain control by requiring them to hold a substantial amount of the network's native cryptocurrency.
- Delegated Proof-of-Stake (DPoS): DPoS allows token holders to elect delegates who validate transactions. This can lead to faster transaction times and lower fees.
- Practical Byzantine Fault Tolerance (pBFT): pBFT is designed to handle Byzantine failures, where some nodes may be malicious or faulty. It provides strong guarantees of consistency and availability, even in the presence of malicious actors.
- Auditing Procedures:
- Smart Contract Audits: Independent security audits of smart contract code are crucial to identify and fix vulnerabilities before deployment. Reputable auditing firms should conduct these audits.
- Code Reviews: Peer code reviews by experienced developers can help identify potential security flaws.
- Bug Bounties: Implementing bug bounty programs incentivizes security researchers to find and report vulnerabilities.
- Regular Security Assessments: Periodic penetration testing and vulnerability scanning should be conducted to identify and address potential weaknesses.
Implementing Best Practices for Securing a Blockchain Voting System
Implementing best practices is crucial to creating a secure and trustworthy blockchain voting system. These practices encompass key management, access control, and ongoing security measures.
- Key Management:
- Secure Key Generation: Private keys should be generated using cryptographically secure random number generators (CSPRNGs).
- Hardware Security Modules (HSMs): Storing private keys in HSMs provides a high level of security by protecting them from unauthorized access.
- Multi-Signature Wallets: Requiring multiple signatures for transactions can mitigate the risk of a single point of failure.
- Key Rotation: Regularly rotating private keys can limit the impact of a potential compromise.
- Access Control:
- Role-Based Access Control (RBAC): Implementing RBAC ensures that users have only the necessary permissions to perform their roles.
- Voter Authentication: Strong voter authentication mechanisms, such as multi-factor authentication (MFA), are essential to prevent unauthorized access.
- Least Privilege Principle: Granting users only the minimum necessary access rights reduces the potential attack surface.
- Monitoring and Incident Response:
- Real-time Monitoring: Continuously monitoring the system for suspicious activity is essential for detecting and responding to attacks.
- Security Information and Event Management (SIEM): Implementing a SIEM system can help collect, analyze, and correlate security events.
- Incident Response Plan: Having a well-defined incident response plan is crucial for quickly addressing security breaches.
- Regular Backups: Regularly backing up the system's data is essential for disaster recovery.
Implementation and Deployment
Deploying a blockchain voting system involves several critical steps, ranging from setting up the environment to launching the system on a live network. This section Artikels the deployment process, explores suitable blockchain platforms, and provides guidance on creating a user interface for voter interaction. Careful execution of these steps is crucial for ensuring the system's security, reliability, and usability.
Deploying on Test and Live Networks
The deployment process differs slightly between test and live networks, primarily in terms of the resources and validation methods employed. Thorough testing on a test network is essential before deploying on a live network.
- Test Network Deployment: This phase allows developers to test the system's functionality, security, and performance in a controlled environment. It involves the following steps:
- Environment Setup: Configure a local development environment or use a public test network like Goerli (Ethereum) or a test network within Hyperledger Fabric.
- Smart Contract Compilation and Deployment: Compile the smart contracts and deploy them to the test network using tools like Remix, Truffle, or Hardhat.
- Testing: Thoroughly test the system's features, including voter registration, ballot creation, voting, and result verification. This involves creating test accounts and simulating various voting scenarios.
- Iteration and Refinement: Address any bugs or vulnerabilities identified during testing. Iterate on the code and redeploy to the test network as needed.
- Live Network Deployment: Deploying to a live network requires careful planning and execution to ensure a smooth launch. This process includes:
- Auditing: Have the smart contracts audited by a reputable security firm to identify and mitigate potential vulnerabilities.
- Network Selection: Choose a suitable blockchain platform based on the project's requirements (e.g., Ethereum for decentralization, Hyperledger Fabric for permissioned access).
- Configuration: Configure the necessary network parameters, such as gas limits and transaction fees.
- Deployment: Deploy the audited smart contracts to the live network. This may involve using a deployment script or a deployment tool.
- User Interface Integration: Integrate the user interface with the deployed smart contracts, allowing voters to interact with the system.
- Monitoring and Maintenance: Continuously monitor the system's performance and security. Implement a plan for handling potential issues or upgrades.
Blockchain Platforms for Voting Systems
Selecting the right blockchain platform is crucial for a successful voting system deployment. Different platforms offer varying features, trade-offs, and suitability for different use cases.
- Ethereum:
- Features: Decentralized, permissionless, large community, robust smart contract support (Solidity).
- Pros: High degree of decentralization, widely adopted, strong security features.
- Cons: High transaction fees (especially during peak times), scalability limitations.
- Suitability: Ideal for public, transparent voting systems where decentralization is a priority.
- Hyperledger Fabric:
- Features: Permissioned blockchain, modular architecture, support for multiple consensus mechanisms.
- Pros: Scalable, customizable access control, suitable for private or consortium-based voting.
- Cons: Requires more setup and configuration, less decentralized than public blockchains.
- Suitability: Well-suited for organizations or groups that require controlled access and privacy.
- EOS:
- Features: Fast transaction speeds, delegated proof-of-stake consensus, free transactions for users.
- Pros: High throughput, user-friendly for voters, relatively low transaction costs.
- Cons: Less decentralized than Ethereum, governance challenges.
- Suitability: Appropriate for applications needing high transaction speeds and user-friendliness.
- Algorand:
- Features: Pure proof-of-stake, fast transaction finality, environmentally friendly.
- Pros: Efficient, scalable, secure.
- Cons: Relatively new platform, smaller community compared to Ethereum.
- Suitability: A good choice for secure, efficient, and scalable voting systems.
Setting Up a User Interface
A well-designed user interface (UI) is crucial for providing a user-friendly experience for voters. The UI should allow voters to easily register, view ballots, cast votes, and verify results.
- Frontend Technologies:
- Frameworks: React, Angular, or Vue.js are commonly used for building interactive UIs.
- Libraries: Web3.js or Ethers.js are used to interact with the blockchain.
- UI Design Principles:
- Simplicity: The UI should be easy to navigate and understand.
- Clarity: Instructions and labels should be clear and concise.
- Accessibility: The UI should be accessible to all users, including those with disabilities.
- Security: Implement security best practices, such as input validation and secure data handling.
- UI Development Steps:
- Connect to the Blockchain: Establish a connection to the blockchain using Web3.js or Ethers.js.
- Implement Voter Registration: Allow voters to register using a secure process, such as providing a unique identifier or using a digital signature.
- Display Ballots: Present the ballots to voters in a clear and organized manner.
- Enable Voting: Allow voters to cast their votes by interacting with the smart contracts.
- Display Results: Provide real-time or delayed results in a transparent and verifiable format.
- Security Considerations: Ensure the UI is protected against common attacks, such as phishing and cross-site scripting (XSS).
Testing and Auditing

Thorough testing and auditing are paramount in the development of a blockchain voting system. These processes are crucial to guarantee the system's reliability, security, and integrity. Rigorous testing helps identify and rectify potential vulnerabilities, ensuring that the voting process functions as intended and that votes are accurately recorded and tallied. Auditing, on the other hand, provides an independent assessment of the system's code and design, verifying its adherence to security best practices and identifying any potential weaknesses that could be exploited.
Neglecting these steps can lead to severe consequences, including the manipulation of election results, loss of voter trust, and legal ramifications.
Importance of Testing and Auditing
The importance of testing and auditing stems from the immutable nature of blockchain and the sensitive nature of voting data. Once a transaction is recorded on the blockchain, it is virtually impossible to alter it. This characteristic underscores the need for robust testing and auditing to ensure that all aspects of the voting system, from vote casting to result tallying, are functioning correctly and securely before deployment.
- Preventing Manipulation: Comprehensive testing helps identify and mitigate potential vulnerabilities that could be exploited to manipulate the voting process. This includes preventing unauthorized access to voting data, ensuring that votes cannot be duplicated, and verifying that the tallying process is accurate and tamper-proof.
- Ensuring Accuracy: Testing validates the system's ability to accurately record, store, and tally votes. This involves testing various scenarios, including different voting patterns, potential errors in user input, and system failures, to ensure that the system consistently produces correct results.
- Building Trust: Rigorous testing and auditing build trust among voters and stakeholders. By demonstrating that the system has been thoroughly vetted and is secure, developers can instill confidence in the fairness and integrity of the voting process. Transparency in these processes is crucial for building public trust.
- Compliance and Legal Considerations: Depending on the jurisdiction, blockchain voting systems may be subject to specific regulations and legal requirements. Testing and auditing help ensure compliance with these requirements and can mitigate legal risks.
Test Case Design
Designing effective test cases involves considering various scenarios to ensure the system's robustness and reliability. Test cases should cover all aspects of the voting process, from user interaction to data storage and result calculation. The goal is to identify potential bugs, vulnerabilities, and performance issues before the system is deployed.
Here's a breakdown of test cases for different aspects of a blockchain voting system:
- Vote Casting:
- Valid Vote Submission: Verify that a valid vote, with all required information, is successfully recorded on the blockchain. Test with different valid options for the candidates.
- Invalid Vote Submission: Test the system's response to invalid votes, such as those with missing information, duplicate votes, or votes cast outside the voting period.
- User Authentication: Test the authentication process to ensure that only authorized voters can cast votes. Verify that the system correctly identifies and rejects unauthorized attempts.
- Voting Period Enforcement: Ensure that votes are only accepted during the designated voting period and rejected before or after the set times.
- Network Connectivity: Simulate network issues and verify that the voting process is resilient to connectivity problems.
- Vote Verification:
- Vote Integrity: Verify that votes are stored correctly and cannot be altered after submission. Test with different vote sizes and data formats.
- Vote Privacy: Ensure that the system protects voter privacy by preventing the linking of votes to specific voters.
- Auditability: Verify that the system provides an auditable trail of all transactions, allowing for independent verification of the voting process.
- Decentralization: Test the system's resilience to attacks by verifying that the voting process remains operational even if some nodes are compromised or unavailable.
- Result Tallying:
- Accurate Tallying: Verify that the system accurately tallies the votes and produces correct results. Test with different voting patterns and large datasets.
- Transparency: Ensure that the tallying process is transparent and auditable, allowing stakeholders to verify the results.
- Tamper-Proofing: Verify that the results cannot be manipulated or altered after the tallying process is complete.
- Performance: Test the system's performance under heavy load to ensure that the tallying process is efficient and scalable.
Vote casting tests verify the ability of voters to successfully cast their votes.
Vote verification tests focus on the ability to verify the integrity and authenticity of cast votes.
Result tallying tests validate the accuracy and integrity of the vote counting process.
Audit Process for Smart Contracts and Systems
Auditing involves a comprehensive review of the smart contract code and the overall system design by an independent third party. The auditor examines the code for security vulnerabilities, logical errors, and adherence to best practices. The audit process typically includes the following steps:
- Code Review: The auditor examines the smart contract code line by line, looking for potential vulnerabilities such as:
- Reentrancy Attacks: Where malicious code can repeatedly call a function before the initial call completes.
- Arithmetic Overflows/Underflows: Errors that can occur when mathematical operations exceed the maximum or minimum value of a data type.
- Denial-of-Service (DoS) Attacks: Where an attacker can disrupt the functionality of the contract.
- Formal Verification: Using formal methods to mathematically prove the correctness of the code and ensure that it behaves as expected.
- Security Testing: Conducting penetration testing and fuzzing to identify security vulnerabilities.
- Documentation Review: Reviewing the project's documentation to ensure that it is complete, accurate, and provides sufficient information about the system's functionality and security features.
- Report Generation: The auditor produces a detailed report outlining the findings, including identified vulnerabilities, recommendations for remediation, and an overall assessment of the system's security.
- Remediation and Retesting: The development team addresses the vulnerabilities identified in the audit report and the system undergoes retesting to ensure that the fixes are effective.
An example of a successful audit is the one conducted on the "Augur" platform. Augur is a decentralized prediction market platform. The audit, performed by Zeppelin Solutions, focused on the smart contracts that govern the platform's functionality. The audit identified several vulnerabilities and provided recommendations for remediation. By addressing the issues raised in the audit, Augur improved its security posture and increased user confidence in the platform.
The audit process is crucial for ensuring the security and reliability of blockchain voting systems. It helps identify and mitigate potential vulnerabilities, allowing developers to build more secure and trustworthy applications.
Scalability and Performance Optimization
![[200+] Coding Backgrounds | Wallpapers.com [200+] Coding Backgrounds | Wallpapers.com](https://teknowise.web.id/wp-content/uploads/2025/10/coding-1024x836-10.jpg)
Scalability and performance are critical aspects of any blockchain voting system, particularly when aiming for widespread adoption and the ability to handle a large number of voters. As the number of participants and transactions increases, the system's efficiency can be significantly impacted. Addressing these challenges proactively ensures a smooth and reliable voting experience for all users.
Challenges of Scaling Blockchain Voting Systems
The inherent characteristics of blockchain technology pose significant challenges to scaling voting systems. These challenges must be carefully considered and addressed to ensure the system can handle a large number of voters and transactions without compromising performance or security.
- Transaction Throughput Limitations: Blockchains, especially those utilizing Proof-of-Work (PoW) consensus mechanisms, have limitations on the number of transactions they can process per second (TPS). This can lead to delays in vote confirmations and overall system responsiveness during peak voting periods. For example, Bitcoin typically handles around 7 TPS, while Ethereum, with its more advanced features, can handle significantly more, but still faces scalability limitations.
- Storage Capacity: Storing all voting data directly on the blockchain can quickly consume significant storage space, leading to increased costs and potentially slower performance. The size of the blockchain grows with each transaction, making it more difficult for nodes to sync and validate the data.
- Network Congestion: During voting periods, the network can become congested, increasing transaction fees and confirmation times. This can particularly affect systems that rely on a public blockchain, where competition for block space is high.
- Consensus Mechanism Bottlenecks: The consensus mechanism used by a blockchain can introduce bottlenecks. PoW, as mentioned earlier, is inherently slow. Proof-of-Stake (PoS) and other more advanced consensus mechanisms offer improvements, but they still require significant processing power and network bandwidth.
- Computational Complexity: Complex smart contracts and intricate voting logic can increase the computational load on the network, leading to slower processing times and higher gas fees (in the case of Ethereum).
Strategies for Optimizing System Performance
Several strategies can be employed to optimize the performance and scalability of blockchain voting systems, allowing them to handle a larger volume of transactions and voters.
- Off-Chain Storage: Utilize off-chain storage solutions, such as IPFS (InterPlanetary File System) or centralized databases, to store voting data that does not necessarily need to be on the blockchain. This reduces the amount of data stored on the blockchain, improving performance and reducing costs. Only essential information, such as the vote hash or a pointer to the off-chain data, is stored on the blockchain.
- Sharding: Implement sharding to divide the blockchain into smaller, more manageable pieces (shards). Each shard processes a subset of transactions, allowing for parallel processing and significantly increasing the overall transaction throughput. This strategy is being actively developed for Ethereum 2.0, aiming to improve scalability.
- Layer-2 Solutions: Explore Layer-2 solutions, such as sidechains or state channels, to process transactions off the main blockchain. These solutions can provide faster transaction speeds and lower fees. Sidechains are independent blockchains that run parallel to the main chain, while state channels allow for off-chain transactions between participants.
- Optimized Smart Contracts: Develop efficient and optimized smart contracts. This includes using efficient data structures, minimizing computational complexity, and optimizing gas usage. Regular audits and security checks are essential to ensure the smart contracts are performing optimally.
- Data Compression: Implement data compression techniques to reduce the size of data stored on the blockchain. This can help to minimize storage costs and improve transaction processing times.
- Consensus Mechanism Selection: Choose a consensus mechanism that offers higher throughput and scalability. PoS and Delegated Proof-of-Stake (DPoS) are often preferred over PoW for their efficiency.
- Caching: Implement caching mechanisms to store frequently accessed data, reducing the need to repeatedly fetch data from the blockchain. This can significantly improve the responsiveness of the system.
Examples of Successful Blockchain Voting Systems and Scalability Solutions
Several blockchain voting systems have been successfully implemented, showcasing various approaches to address scalability challenges. Analyzing these examples provides valuable insights into practical solutions.
- Follow My Vote: Follow My Vote utilizes a hybrid approach, combining a blockchain with off-chain data storage. They store the voting records off-chain and only store the cryptographic hashes of the votes on the blockchain. This reduces the on-chain storage requirements and improves scalability. They have conducted successful pilot projects and provided a transparent and auditable voting process.
- Voatz: Voatz employs a mobile voting platform and leverages a permissioned blockchain to ensure security and auditability. They utilize features such as biometric authentication and advanced encryption to secure the voting process. While specific scalability solutions aren't always publicly detailed, the use of a permissioned blockchain and centralized components likely contributes to their ability to handle a large number of voters.
- Agora: Agora uses a combination of blockchain technology and identity management to create a secure and transparent voting system. They focus on user verification and authentication, and while specifics of their scalability solutions are not always fully disclosed, their architecture is designed to be scalable.
- Polys: Polys provides a platform for conducting online voting using blockchain technology. They focus on ease of use and offer various features for managing the voting process. They often use a permissioned blockchain or a hybrid approach to manage scalability.
These examples demonstrate the importance of adopting tailored solutions to achieve scalability and performance in blockchain voting systems. The choice of strategies depends on the specific requirements of the voting system, including the number of voters, the desired level of security, and the available resources.
Legal and Regulatory Considerations
Implementing a blockchain voting system introduces a complex web of legal and regulatory hurdles. Navigating these frameworks is crucial for ensuring the legitimacy, security, and ultimately, the success of such a system. Different jurisdictions possess varying approaches, demanding careful consideration and adaptation to local laws. Compliance is not just a matter of ticking boxes; it's about building trust and demonstrating accountability to voters and regulators alike.
Legal and Regulatory Frameworks in Different Jurisdictions
The legal landscape surrounding blockchain voting varies significantly across the globe. There's no one-size-fits-all approach. Some countries are actively exploring and promoting blockchain voting, while others remain hesitant or have yet to establish clear guidelines. This disparity creates both opportunities and challenges for developers and implementers.
- United States: The legal status of blockchain voting in the US is fragmented. While there's federal interest, the primary regulation falls to individual states. States like West Virginia have experimented with mobile blockchain voting for military personnel and overseas citizens. However, concerns remain regarding voter verification, ballot secrecy, and the potential for manipulation. The Election Assistance Commission (EAC) plays a role in setting standards, but its influence is limited.
- European Union: The EU has a more cautious approach. The General Data Protection Regulation (GDPR) has implications for data privacy in blockchain voting, particularly regarding the storage and processing of personal voter information. The EU is actively exploring blockchain applications, but the regulatory environment is still evolving. There is a focus on interoperability and data protection, creating significant hurdles for the implementation of blockchain voting.
- Other Jurisdictions: Countries like Switzerland have shown more openness to blockchain voting, with some cantons experimenting with the technology. However, even in these jurisdictions, comprehensive legal frameworks are still under development. Other nations are watching and learning, but widespread adoption remains uncertain.
Compliance Requirements for Blockchain Voting Implementation
Implementing a blockchain voting system requires meticulous attention to compliance requirements. These requirements span various aspects of the system, from voter registration and verification to data security and auditability. Failure to comply can lead to legal challenges, reputational damage, and the invalidation of election results.
- Voter Registration and Verification: Ensuring the integrity of voter registration is paramount. This involves verifying voter identities, preventing duplicate registrations, and protecting against fraudulent activities. Compliance with Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations, where applicable, is crucial. Strong identity verification mechanisms, such as multi-factor authentication and biometric verification, are essential.
- Data Security and Privacy: Blockchain voting systems must adhere to stringent data security and privacy standards. This includes protecting voter data from unauthorized access, breaches, and manipulation. Implementing encryption, access controls, and regular security audits are critical. Compliance with GDPR and other data privacy regulations is essential.
- Auditability and Transparency: Blockchain technology's inherent transparency is a key advantage. However, it's essential to design the system to facilitate comprehensive audits. This includes providing mechanisms for verifying the integrity of the blockchain, tracking transactions, and generating audit trails. Open-source code and public access to audit logs can enhance transparency and build trust.
- Accessibility and Inclusivity: Voting systems must be accessible to all eligible voters, including those with disabilities. This requires ensuring that the system is user-friendly, provides alternative voting methods, and complies with accessibility standards.
- Election Integrity and Security: Maintaining the integrity of the election process is crucial. This involves protecting against cyberattacks, ballot tampering, and other forms of election interference. Implementing robust security measures, such as secure coding practices, penetration testing, and vulnerability assessments, is essential.
Current State of Adoption and Future Outlook
The adoption of blockchain voting is still in its early stages. While there's significant interest and potential, widespread implementation faces considerable challenges. The future outlook depends on several factors, including technological advancements, regulatory developments, and public acceptance.
- Pilot Projects and Experiments: Numerous pilot projects and experiments are underway globally. These projects are testing the feasibility, security, and usability of blockchain voting systems in various contexts. These real-world tests provide valuable insights and data to refine the technology and address practical challenges.
- Technological Advancements: Continued innovation in blockchain technology is essential. This includes improvements in scalability, security, and user experience. Advancements in areas such as zero-knowledge proofs and homomorphic encryption can enhance privacy and security.
- Regulatory Clarity: Clear and consistent regulations are crucial for accelerating adoption. This requires governments and regulatory bodies to develop frameworks that address the unique challenges of blockchain voting. This includes defining standards for voter verification, data security, and auditability.
- Public Trust and Acceptance: Building public trust is paramount. This involves educating voters about the technology, addressing concerns about security and privacy, and demonstrating the benefits of blockchain voting. Transparency and open communication are key to building trust.
- Potential Future Scenarios:
- Gradual Adoption: A slow but steady adoption, with blockchain voting being implemented in specific use cases, such as overseas voting or internal elections, before being used for larger-scale elections.
- Rapid Adoption: A more aggressive adoption fueled by significant technological breakthroughs, supportive regulatory frameworks, and strong public demand.
- Hybrid Systems: The emergence of hybrid systems that combine blockchain technology with existing voting infrastructure.
Final Summary
In conclusion, mastering "How to Coding Blockchain Voting System" empowers you to build voting systems that are secure, transparent, and auditable. This guide equips you with the knowledge to design, develop, and deploy a blockchain voting system, providing a pathway to improve the integrity of elections. As the technology continues to evolve, understanding these principles is crucial for shaping a more democratic and trustworthy future.